Introduction
MITRE ATT&CK® is one of the huge topic in itself. I am writing this article from a beginner's perspective. If you are new to this then you are at the right place.This framework is useful for both Red team and Blue team but I am giving more focus on Blue team through this article. This is one of the important topics you have to learn if you want to start your career in the Red team or Blue team. It gives you a real-world observation.
So, let's start with the MITRE Introduction and then go step by step. I hope this article is helpful for you.
What is MITRE?
The Mitre Corporation (stylized as The MITRE Corporation and MITRE) is an American not-for-profit organization. It manages Federally Funded Research and Development Centers (FFRDCs) supporting various U.S. government agencies in the aviation, defense, healthcare, homeland security, and cybersecurity fields, among others.MITRE Corporation has created some projects/ research for the cybersecurity community specifically:
- ATT&CK® (Adversarial Tactics, Techniques, and Common Knowledge) Framework
- CAR (Cyber Analytics Repository) -Knowledge Base
- SHIELD -Active Defense
- AEP (ATT&CK Emulation Plans)
What is the ATT&CK Framework?
MITRE ATT&CK® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The relationship between tactics and techniques can be visualized in the ATT&CK Matrix. The ATT&CK® framework has grown and expanded throughout the years. It is used by both Red Team and Blue Team.The basic terminologies will often hear when dealing with the framework, threat intelligence etc. are as follows:
- APT (Advanced Persistent Threat): This can be considered a team/group (threat group) or even country (nation-state group), that engages in long-term attacks against organizations and/or countries.
- Tactic: The Tactic is the adversary’s goal or objective such as Persistence, Execution, Privilege Escalation, Initial Access etc.
- Technique: The Technique is how the adversary achieves their goal or objective by performing an action. For example, an adversary may dump credentials to gain access to useful credentials within a network that can be used later for lateral movement.
- Procedure: The Procedure is how the technique is executed.
As a beginner when you start to study how a cyberattack happens, we are told to learn about Cyber Kill Chain. If there is an easy model like Cyber Kill Chain then why Security Researchers had created an ATT&CK®. This question comes to mind, right?? So let's deep dive into it.
Why ATT&CK was Created?
MITRE started ATT&CK in 2013 to document common Tactics, Techniques, and Procedures (TTPs) that Advanced Persistent Threat groups use against Windows enterprise networks.This started with an internal project known as FMX (Fort Meade Experiment). Within this project, selected security professionals were tasked to emulate adversarial TTPs against a network, and data was collected from the attacks on this network and that gathered data had been used to construct the beginning pieces of the ATT&CK® Framework.
ATT&CK® Framework was created to address the following four main issues.
- Adversary behaviors- Adversary’s tactics and techniques allowed researchers to develop analytics to detect possible adversary behaviors. Typical indicators such as domains, IP addresses, file hashes, registry keys, etc. were easily changed by adversaries and were only useful for point in time detection. They didn’t represent how adversaries interact with systems.
- Lifecycle Models- Existing adversary lifecycle and Cyber Kill Chain concepts were too high level to relate behaviors to defenses. The level of abstraction wasn’t useful to map TTPs to new types of sensors.
- Applicability to real environments- TTPs need to be based on observed incidents to show the work is applicable to real environments.
- Common Taxonomy- TTPs need to be comparable across different types of adversary groups using the same terminology.
Different Models before MITRE ATT&CK:
1. Cyber kill chain
The Cyber Kill Chain is more than a model for an attack. The seven phases of the Cyber Kill Chain provide an excellent foundation for any organization’s security design.
Difficulties with the Cyber Kill Chain. The Cyber Kill Chain does not focus enough on what to do after an attacker has broken into your network successfully.
- The Cyber Kill Chain’s phase sequence cannot accurately depict all attacks as several kill chain phases can be bypassed entirely.
- The Cyber Kill Chain assumes a traditional perimeter-focused defense where a firewall is the main line of defense and so fails to cover other attack vectors and internal attack paths; modern organizations need to leverage defensive solutions within the perimeter.
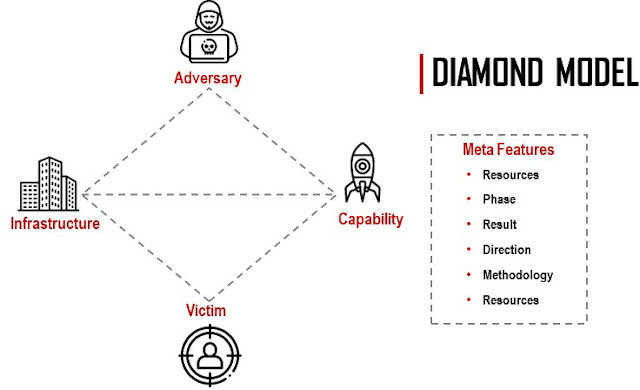
2. Diamond Model
The Diamond Model comes from a different time when there was more of a focus on analytic outcomes than process and principles.The Diamond Model is still useful today. While ATT&CK primarily documents adversarial behavior, the Diamond Model is more useful for clustering intrusions for analysis. These separate strengths are complementary; mapping attack techniques within the ATT&CK matrix should prove useful data for the Diamond Model when analyzing a threat actor’s capabilities.
The Diamond Model and the MITRE ATT&CK framework both add value to cyber threat intelligence but very differently. However, while the ATT&CK Framework adds value to cyber threat intelligence through the study of used tactics, techniques, and tools, the Diamond Model adds value to cyber intelligence through a deep understanding of the infrastructure and capabilities of both victim and adversary.
MITRE ATT&CK® Framework is basically designed for Enterprise and Mobile. When we explore more on mitre.org website we can see the ATT&CK® Framework for both. TTP’s are different for both of them. But our focus is on ATT&CK® Framework for Enterprise. So, let's learn about it.
MITRE ATT&CK® Framework for Enterprise:
Below image shows ATT&CK® Framework for Enterprise. Across the top of the matrix, there are 14 categories which are Tactics. Each category contains the techniques an adversary could use to perform the tactic. The categories cover the seven-stage Cyber Attack Lifecycle (credit Lockheed Martin for the Cyber Kill Chain). Some of the techniques have sub-techniques also. We can see that at https://attack.mitre.org/matrices/enterprise/.At the time of this writing, there are 188 techniques & 379 sub-techniques are in the Enterprise model. MITRE regularly updates ATT&CK with the latest and greatest hacking techniques that hackers and security researchers discover in the wild.
MITRE ATT&CK Matrices:
- Pre-ATT&CK: Focuses on "pre-exploit" adversarial behavior. Pre-ATT&CK is included as part of the ATT&CK for Enterprise matrix.
- ATT&CK for Enterprise: Focuses on adversarial behavior in Windows, Mac, Linux, and Cloud environments. The Enterprise ATT&CK matrix, the most commonly referenced matrix, combines six separate matrices: Windows, macOS, Linux, Cloud, Network, Containers.
- ATT&CK for Mobile: Focuses on adversarial behavior on iOS and Android operating systems.
- ATT&CK for ICS: Focuses on adversarial behavior within an ICS (Industrial Control Systems) network.
ATT&CK® and Threat Intelligence:
Threat Intelligence (TI) or Cyber Threat Intelligence (CTI) is the information, or TTPs, attributed to the adversary. By using threat intelligence, as defenders, we can make better decisions regarding the defensive strategy.Understanding the Pyramid of Pain concept as a Threat Hunter, Incident Responder, or SOC Analyst is important. We are learning here this Pyramid of Pain concept because the ATT&CK® works on TTP’s level i.e., the top layer level.
The Pyramid of Pain shows how difficult it is for an attacker to circumvent the particular method that has been taken away from them.
Above figure shows how cyber defenders might view IOCs in their networks. It shows the pain it will cause the adversary when we are able to deny those indicators to them.
Changing Hash value of any malicious file, IP addresses and Domain names is quite simple for an adversary. Hash values can be easily altered by employing polymorphic or metamorphic techniques. Adversaries use Tor, VPNs, and anonymous proxies to spontaneously and effortlessly change IP addresses.
Unlike IP addresses, domain names are difficult to change as they require tariff or pre-registration. However, by using dynamic domain name system (DDNS) services and domain-generated algorithms (DGA), threat actors can automatically modify domain names with APIs. Attackers find bypassing domain name regulations easy.
Network Artifacts such as user-agent string, C2 information, or URI patterns followed by the HTTP POST requests etc. and Host Artifacts such as suspicious process execution, registry objects, files dropped by malicious applications etc. When we detect, the attacker will feel a little more annoyed and frustrated because the attacker would need to go back and change his/her attack tools and methodologies.
Taking away an attacker’s tool is challenging as they will have to devise a new way of carrying out their objectives. At the top of the Pyramid of Pain, are the Tactics, Techniques, and Procedures that the ATT&CK Framework documents. Using MITRE ATT&CK we can find out the TTP’s that the adversary had used. Once we get the TTP’s, the attacker has only two options. Either go back, do more research and training, reconfigure their custom tools or give up and find another target.
Scenario:
You are a security analyst who works in the aviation sector. Your organization is moving their infrastructure to the cloud. Your goal is to use the ATT&CK® Matrix to gather threat intelligence on APT groups who might target this particular sector and use techniques targeting your areas of concern. You are checking to see if there are any gaps in coverage. After selecting a group, look over the selected group's information and their tactics, techniques, etc.
What are the benefits of using the MITRE ATT&CK Framework with your SIEM?
SIEM vendors are always on the lookout for ways to improve their solution to gain more insights and information that can help detect and respond to an attack.
The ATT&CK Framework is beneficial throughout an organization. It’s a great tool for communicating with senior leadership and security managers. Using ATT&CK, it’s much easier to produce a more accurate overview of incidents. When alerts correspond to an ATT&CK technique, security analysts can more quickly understand how an alert relates to a larger attack so they can take the necessary steps to protect their business.
Conclusion:
The MITRE ATT&CK® Framework teaches us that organizations must be mindful that “It is not IF an organization will be attacked but it’s about WHEN it will be attacked!”. The ATT&CK® Framework is useful not only for Defenders but also for Red Teamers. Every SIEM solution has this ATT&CK® Framework. The more information we have as defenders, the better we are equipped to fight back. If anybody wants to build their career as SOC Analyst, Detection Engineer, Cyber Threat Analyst etc. these tools or resources are must to know.References:
Priyanka Malvi
( Security Analyst)








0 Comments