Wi-Fi networks are
designed by knowledgeable IT professionals but that doesn't mean that they are
completely safe. Today, we'll
show how a malicious twin attack could take Wi-Fi passwords and kick users off
their preferred network, while creating a fake one. The victim is then forced to join the fake network, and
provide the Wi-Fi password in order to gain internet access.
Although a more
knowledgeable user could spot this kind of attack, it's actually quite
efficient against people who aren't trained to spot suspicious activity on the
network. The
reason this is so effective is that the majority of users aren't sure what a genuine
software update is, which leads to confusion when they realize the presence of
an attack development.
What is an Evil Twin
Attack?
An evil twin is form
of Wi-fi attack which takes advantage of the majority of devices and
smartphones, where one can only view just the "name" or ESSID of the
wireless network. This can
make it difficult to differentiate between wireless networks that have the same
name, and the same type of encryption.
Indeed the majority of
networks include multiple network-extending access points that all share the
same name, allowing for greater access, but without making it difficult for
users to distinguish between them.
If you're interested in
seeing what happens, make a Wi-Fi hotspot in your smartphone and label it with
the same name as your home network. Once you do this, you'll find it difficult
to discern the distinction between the two networks, or your computer might
simply view both networks as being the same.
A network sniffing tool
for networks such as Wireshark or Tcpdump will clearly show the differences between these
networks, however to the average person they will appear identical.
This is a great way to
trick users into connecting if you have a network that has the identical name. But
the problem here is, we don't have the password? We can't build a network to fool the user
into connecting by itself, but we could use a technique called social engineering and attempt to make the user provide us with the password,
by getting them removed from the actual network.
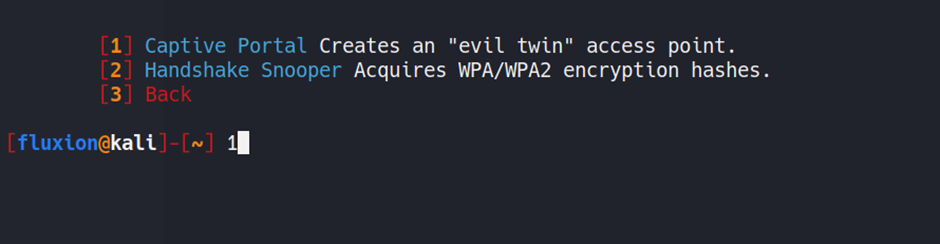
What is Fluxion?
Fluxion is a tool which
can be used to conduct penetrating Testing and Security Auditing on Wireless
Access Points (WAP). It
employs Social Engineering to grab the authentication password from users.
It attempts to collect the
WPA/WPA2 keys from the targeted Access Point by performing a Phishing attack. Two types of attacks can be carried out
with Fluxion. One of these is an attack
known as the Handshake Snooper attack, and the other is the Captive Portal.
We’ll talk more about these attacks in the coming paragraphs.
Step-1 Installing Fluxion
We now have a better
understanding of the Fluxion tool's capabilities, so it is time for us to
install it on our computer. This demonstration will be done with Kali Linux.
Fluxion does not come with
Kali Linux as a default, and there is no way to get it. We will need to clone its repository from
Github.
It contained directories
like attacks, bin, docs, and docs as well as a shell script called fluxion.sh. In the previous versions, the file was
different. Now you only need to add the parameter "-i" to install and
check for dependencies.
git clone https://github.com/FluxionNetwork/fluxion.git
cd fluxion
ls
./fluxion.sh -i
If
you are a root user then you can directly use ./fluxion.sh , otherwise you need
to use the command
sudo
./fluxion.sh
After using the above command, we'll be welcomed with the logo of the Fluxion, and it will automatically start examining the dependencies needed on its own. If any dependencies that are marked as missing, it's advised to install them yourself.
In this particular
instance we have all the dependencies installed , so we can now successfully
run the tool.
Step-2 Selecting the Target
After, the successful installation of
the dependencies we would then be presented with a language selection menu. We'd like to
select English so we'll enter the desired number in the selection menu , and
then press the Enter.
We now need to choose which attack, we would like to carry out to an Access Point. We must record the handshake that occurs between the router in the network and the actual user. We will then use the handshake to verify and attempt to gain the credential needed to access the Access Point.
Therefore, we'll need to
choose that Handshake Snooper. This Handshake Snooper attack attempts to recover the
authentication hashes for WPA and/or WPA2 (the 4 way handshake) and then use
them in the Captive Portal for key verification.
After choosing the wireless attack type, we need to select the Channel that is intended to be
monitored. Because a large number of
Wireless Access Points in current times can range from 2.4GHz to 5GHz, so we
should select all channels within the range.
After selecting ‘Option 3’ , it will show a brand new window that is illustrated on the picture
below. This is done after scanning every
possible target within the network reach.
Make sure that you allow
the process to continue for a few minutes until you can see your target within
the window. Press
Ctrl + C when you have located your target.
Step-3 Capturing a Handshake
After completing the previous step and
terminating the fluxion scanner after discovering our target network, we are
back on our main terminal. Based on the process we used previously we'll be
able to access the Wi-Fi List with our target. In our
example we will target the Intelliroot Wi-Fi. Therefore, we input the number in the next step.
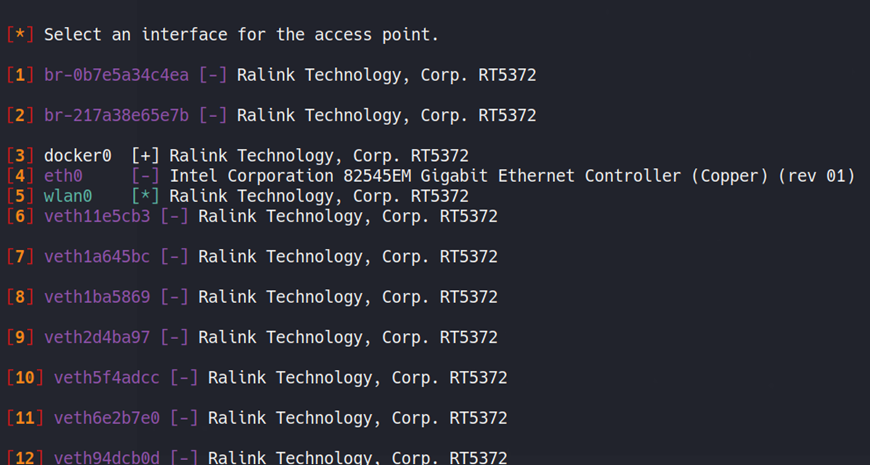
We will now be asked about the interface
for tracking targets. If, within your network you have a different wireless
interface you wish to use to perform target tracking, then choose that interface. In our case, we're going to use the wlan0 interface to
perform tracking too.
But I know most of you would be confused,
so you can simply select the skip option and let fluxion decide it
by itself. To make this tutorial much easier for you, we’ll be using the skip
option.
Now, we are at a point in which we have to choose the method of handshake retrieval. There are three options offered by Fluxion. The first method is called Monitor or passive mode. The passive approach makes us go quiet, making the attack undetectable or invisible and allows for more effective listening.
This technique is best when the target is located far away from us but the drawback is that the device has to listen until it is connected to the target access point.
This could take a considerable amount of time. The two other methods, aireplay-ng deauthentication as well as mdk4 are extremely aggressive. They employ the deauthenticator.
They send deauthentication packets to devices or users that are connected to the target access point. This method is a bit contentious since it blocks connections between access point and the users.
When the connection is blocked or disconnected , a few users will attempt to connect with the device, which will transmit the 4-way handshake, however this time Fluxion will capture that handshake.
It is your choice to use either of these methods as they work equally well. We will however make use of the mdk4 technique.
The next step is to choose which tool to use to check the hash of the authentic handshake.
We can
observe that the aircrack-ng approach is regarded as unreliable because it
hasn't been updated in several years, so we’ll opt for the cowpatty method
since it is suggested by Fluxion itself.
As we move down further, our steps become
easier as fluxion keeps recommending the best options for us and we just have
to choose them.
The next step is to choose the
verifier's synchronicity. It determines the method of verification that
happens with the recording of data. It asks whether we wish to record data
asynchronously or synchronously.
It’s necessary to understand the difference between these two.
Asynchronous: Asynchronous option will start the verification process
while the system is taking in data. Because this is multitasking on an
upper level, it requires more threads. If you're running an aggressive OS
like Kali Linux direct on your system, then you are able to use it. However, if
you're operating Kali Linux using a virtual Machine as we do, it may cause
issues as there are a limited number of threads that can be used by Kali.
This Synchronous option will not capture data prior to trying to verify
the handshake. Because this isn't multitasking, it won't cause problems
when you have a low number of threads. There is however an issue with
these options as they end the process of capturing data and you may lose some
handshakes. But you needn’t worry as we had already decided to verify the
verifier each 30 seconds and not miss any handshakes.
Go for the synchronous one if you are running kali on a VM, if you have a high specs system or have Linux directly installed as an OS then you should go with the asynchronous option.
Step-4 Gathering the
Handshake/Handshake Snooper Attack
Now, the attack begins and a new window pops up. This window is called, “Handshake Snooper Arbiter Log”. This one is the log viewer.
It shows the events in the order they start. The process of deauthenticating all clients will begin, and in a only a few minutes, all the customers will have been disconnected from their Wi-Fi devices. When any of these users or devices attempt to reconnect to the Wi-Fi, we'll be able to record the handshake.
As, we see that the attack
worked and we managed to obtain an acceptable hash. Now, we shut down the viewer in order to start
the next phase of our attack.
As, we have recorded the
handshake, it is possible to utilize this handshake for the Captive Portal
Attack which is sometimes referred to in as The Evil Twin Attack. As, we close the Handshake Log window, we
are asked whether we would like to choose an additional attack, as shown below.
We will select the 1 option, as we want to start a new attack.
Step-5 Starting the Captive Portal
Attack
Captive Portal Attack or
as we usually refer to it The Evil Twin Attack, is the kind of attack in which
we attempt to steal the access point's WPA/WPA2 password by utilizing a rogue
internet using an authorization portal that collects the credentials.
After having captured the
handshake using Handshake Snooper the user will be again redirected to the main
menu of fluxion like before. But this time we will this choose the Captive Portal.
Fluxion is an amazing tool as it had already detected the
access point of our target after capturing the handshake. So, we will select the Yes or ‘Y’ option.
Fluxion now requests us to
choose an interface for target tracking. If you're in a location that has numerous wireless
interfaces that could be used to tack select the one you prefer. If not, you can skip this step by selecting option 2.
Now we need to select the
wireless connection that Fluxion will use to transmit the signals for
de-authentication. Because
we require a wireless interface, we'll select the wireless network wlan0. Don’t
worry, you won’t be overwhelmed with so many interfaces as shown below, you
would only have a few to choose from.
We now have to decide on
the methods or tools to be used for deauthentication of Wi-Fi users. This is also based on the kind of
environment and individual preferences.
Each of the three
approaches is equally efficient. However, we'll be using the mdk4 method which we used while capturing
handshake in step 3.
As mentioned earlier, we
select the option that fluxion best recommends. Hence the 1st
option, hostapd. There is also another reason for not choosing airbase-ng as it
is slow compared to hostapd.
Now, we choose the hash
verifier method. We’ll go with the option that fluxion recommends the best, i.e. cowpatty also this is the method we used earlier.
At this point we provide
the captured handshake. If the handshake is in the form of a captured file
(.cap) file, you can select the second option and then provide the correct path
of the handshake file.
Since we captured the
handshake using Handshake Snooper, the hash was automatically recognized by
Fluxion. So, we
selected the option of , ‘Use hash found’.
As we
choose cowpatty in the previous steps, then we will again go with the same
option and also it is the most favorable one.
Now, we are required to choose an SSL/TLS certificate source for
our captive portal. You can select the deactivate SSL option, but this will
cause suspicion since the general web portal that is used for captive uses SSL
certificate.
If you've got an SSL certificate,
then fluxion will automatically detect it. As we don't possess one, we decided to create an SSL
Certificate.
As this is a social
engineering attack, we need to be as much precise as possible.
We must now choose the
internet connection type for the rouge network users will connect to. As explained before we’ll go with the recommended option.
You can choose emulated
option but sometimes it creates problem for android and iOS users also the
portal doesn’t appear much authentic.
But if you choose the
disconnected option then, when users connect to our network they will be
presented with a portal that is captive. This doesn’t mean
that the disconnected option is perfect, instead it is less likely to fail.
The next step is to select
our Portal template. As by
default Fluxion has some amazing templates. In most of the situations, users
would be deceived by these templates but sometimes it won’t work with cautious
users.
In our case we'll be using
the general portal using English language.
Step-6 Capture Network Credentials
After the success of Captive Portal attack, fluxion will be able to de-authenticate all users from the
targeted access point. Users will be removed
from their Wi-Fi connection and be shown two networks. One is a real Network and the other is a fake network.
The below image shows how
the attack appears from the perspective of the victim. It is evident that there are two networks
with the identical name Intelliroot.
Now let's resume our attack. When we select the template for the network, we'll notice that multiple
windows pop up. Let's have
a look.
The first one on the left is
The DHCP Service. If the
victim connects to our network it is the duty to the DHCP service to simulate
the connection and assign the IP address for the victim's device.
To the right, we will see
an hostapd Window. This is our Captive Portal. It records the activities of our clients as they visit
through our Captive Portal.
To the right, we will are
able to see an AP Authenticator window. It records information such as the SSID,
MAC, and other details that are relayed by your device to the target's. We can track the attempts made by the user in case they
enter the wrong password. You can view the
list of clients that are connected to our network.
Starting from the down
left side, we've got an option to use the DNS Service. Because we don't provide internet
connectivity, all DNS queries that are generated by your device be handled via
this server.
Moving on the right side,
we can see the logs for the Web Service which is hosted by the victim.
Finally, we are able to
access our Jammer Service that is in charge of deauthenticating the
different devices connected to the specifically targeted Access Point.
As soon as the victim
enters the right password for the target Access Point in the captive portal, we
would be notified in the authenticator window and the attack will finish.
Let’s now look from our victim’s perspective. If you click the rouge network from the Wi-Fi tab in the
previous step , the victim will be shown an in-browser interface that is based
on the template we gave.
It displays the correct
name of this Access Point in the heading. It then asks for the WPA password
from the victim and the victim is required to enter the password, which begins
the process of the four-way handshake.
The hash of the password
is verified with the correct hash that we have captured earlier. If the user typed in the wrong password
then they are required to enter the new password until they are sure that the
hash is matched.
Once the victim has entered the correct password to connect to the Access Point, the victim is then automatically moved from the fake AP to the authentic access point (AP), and the jammer or deauthenticator is stopped.
All users who were blocked
are now able to connect to the correct access point. The captured password is saved at /home/kali/Desktop/fluxion/attacks/Captive
Portal/netlog/ as demonstrated below.
Note: This address can be
different for everyone as it depends on which directory you have your fluxion
tool installed.
Step-7 Checking out the Password
Now we need to check out the saved
password. For that we have to visit the location given by fluxion in the step
above.
As, you can see how interesting this attack was and how easily hackers could manipulate you to give them the passwords for your network.
Defending against Evil Twin Attack
The best method of
protecting against an Evil Twin attack is to educate yourself more about cyber
security threats. There are also a few things to keep in mind like, If you
suddenly lose the possibility of connecting to your trusted network , and suddenly
discover an active wireless network bearing the identical name, they aren't a
coincidence, nor an ordinary occurrence.
You could be a victim of
the sinister Evil Twin Attack!
So, DO NOT ever
connect to an unidentified wireless network that claims as your own,
specifically one that is not encrypted. If you think you’re being frequently disconnected from your
router then switch off your router and turn it on once again.
Thanks for reading this article. If you have any questions or
doubts then please leave a comment and don’t forget to check out more of
Intelliroot cyber security articles.
Written By,
Dhabaleshwar Das
(Security Analyst)




































0 Comments