CVE-2021-41773
Path Traversal and Remote Code Execution in Apache 2.4.49
Apache Server:
Apache
HTTP Server, also known as Apache, is a popular free and open-source web server
program used to serve websites on the internet. It was created and is
maintained by the Apache Software Foundation. Additionally, the Apache software
provides a secure and safe file-sharing function that allows users to store
files in the root directory and share them with other users.
Path
Traversal:
Path
traversal, also known as directory traversal, allows an attacker to access
files and directories that they should not be able to access on a web server.
When an attacker wants to navigate through one or more directory levels in the
current directory, he or she frequently enters characters such as
"..", "../", or "../../". When user input in web
applications allows a user to construct file paths without proper input
validation, a vulnerability occurs.
Remote
Code Execution:
CVE-2021-41773:
On October 4, 2021, Apache published CVE-2021-41773.
Path traversal and Remote Code Execution are features of the Apache 2.4.49 HTTP
server. The flaw stems from the incorrect handling of URL-encoded path
traversal.
URL validation could be bypassed by the encoding
character if the file outside the directory does not set the default
configuration of "Require all denied". It has also been discovered
that if mod_cgi is enabled, the vulnerability allows an attacker to execute
remote code execution.
Exploitation:
Remote Code Execution and Path Traversal
attack POC:
An attacker can use specially crafted requests
beginning with (../) and modified requests containing malicious code to perform
directory traversal and remote code execution.
Apache 2.4.49 httpd.conf vulnerable
configurations:
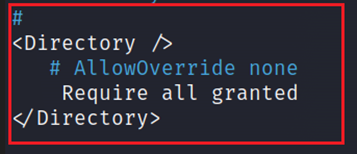
1. 1. Directory Traversal Vulnerable Configuration:
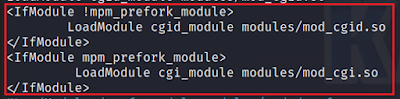
1. 2. Remote Code Execution Vulnerable Configuration:
Vulnerability
can be utilized for remote code execution when mod_cgi is enabled, this is also
not a usual function to enable.
Mitigation:
1. 1. In order to remediate this vulnerability everyone who uses Apache 2.4.49 should make sure they update to the latest release of the Apache HTTP Server.
2. 2. Make Sure that your configuration is:
Required all denied
is the default configuration
Reference:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-41773
https://nvd.nist.gov/vuln/detail/CVE-2021-41773








0 Comments